Imagine going into a shop to browse through some DVDs. You don’t buy one – there’s nothing that takes your fancy. You leave the shop, and go to another. But when you get to the second shop, you find that an assistant from the first shop is standing beside you, watching your actions. Not only that, but this assistant has also made a note of the time you visited the first shop, and logged down everything you looked at, along with the fact that you didn’t buy anything. The assistant from the first shop additionally passes this information on to the assistant in the second shop, who notes it down… Would you tolerate that? If not, then you should know about cookies, how they work, and how you can stop them from stalking you in the virtual world.
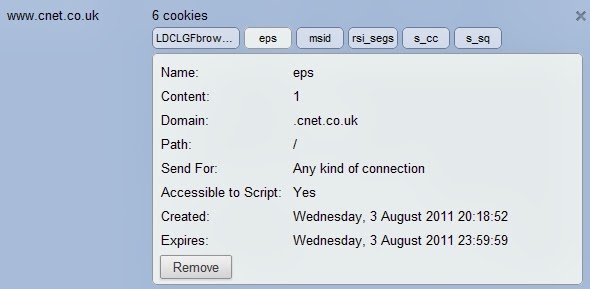
A simple first-party cookie from the site CNet. This cookie was set to expire at the end of the day and would therefore not be considered any great privacy invasion. Some cookies, conversely, have a duration of decades. I took this capture seconds after my first visit to the CNet homepage since enabling cookies for the site. Just from the single homepage visit and with no subsequent clicks, it's apparent that the site has placed six cookies on my system. This is quite normal.
You may have read elsewhere that cookies are small and harmless text files placed on your computer by sites you visit, helping to speed up your browsing experience and making your use of the Internet easier. This sounds innocuous enough, and it can be said to be true. But actually, if you don’t manage your cookies, the effect on your privacy is barely any different from downloading a piece of spyware. The key point is not that the cookies are placed on your system, it’s that they’re read. And they can be read many times, in some cases by different companies – in the process building what could be a comprehensive dossier about the sites you visit, how often you visit them, and what you do when you’re there.
Browsers will accept cookies by default, so unless you’ve specifically taken steps to reset the way your browser handles them, you will be tracked, and you could be tracked by a heck of a lot more people than you may realise.
It’s not just the sites you visit which place and read cookies on your system. Ad servers will place and read cookies too. These are known as third party cookies, because they're set by a web entity other than the site you chose to visit. A company serving ads will not be tied to one website. It will very likely place ads on many of the sites you frequent. So each time you visit a site upon which that ad server places ads, the ad server is potentially able to read the cookies it’s previously placed on your system, and collate the information. Effectively, you're being stalked around the web by people you know very, very little, if anything, about.
If your browser is accepting third party cookies, the first time you view the cookies on your system may come as something of a shock. The first element of that shock will be the sheer number of cookies sitting on your drive. Lots and lots of folders, each containing one or more cookies – usually more, and very frequently a lot more. The second shock will be that a large number of the names on the cookies will be of companies you’ve never heard of. These are the third parties. The ‘invisible’ people the sites you visit give permission to set and read information on your computer, even though you’ve never heard of them, and even though in many cases you don’t even realise they’re there.
Ideally, we could set our browsers to block all cookies. Every browser I’m aware of allows this, and it’s easy to implement. With this option selected, no site you visit can place or read any cookies on your system. Great! Except it's not great, because it makes lots and lots of activities on the web impractically difficult, and makes some impossible. Typically, with all cookies blocked, you won’t be able to use: browser-based email services such as Hotmail or Yahoo Mail, social networking sites, price comparison sites, bill-monitoring services, many forums, blogging and website creation facilities, recruitment sites… And that’s only the tip of a huge iceberg. And because passwords are stored in cookies, you won’t be able to save your site passwords with all cookies blocked. This means typing in your username/email and password every single time you want to log in to any site which requires you to log in. Fine if you only have a couple of logins, but impractical if you have, say, 20 – all with different passwords. If you care about online security, you should have different passwords for every login.
In general (although there are exceptions), if you just want to browse, you can do so without the use of cookies, but if you want to interact or participate, you must at least allow the specific sites you participate in to place and read cookies on your system. The good news is that it’s quite possible to block cookies from all sites and third parties by default, and then select a number of specific sites and allow them, and only them, to place and read cookies. So if you use ImageShack and Twitter for example, you can blanket-block all cookies for every single site on the web, then instruct your browser to individually exempt Imageshack.us and Twitter.com from your block. Cookies can then only be placed or read on your system by the two domains you've exempted. You can use Twitter and ImageShack as you wish, but no other sites have access to your cookie folders. A setup like this makes you extremely difficult to track.
You probably know now whether you care enough about cookies to configure your browser to manage them as described above. If you would like to control web cookies on your system, I'm going to show you how to set up selective blocking using the Mozilla Firefox browser (I'm using version 5, but older versions have the same interface, as does the newer version 6). Please note that if you don't already have Firefox, it works independently of Microsoft's browser, so downloading and installing it will not in any way prevent you from continuing to use Internet Explorer any time you wish. You could even have both browsers running at the same time if you wanted. So you're not taking any risks in giving Firefox a try. Like all the major browsers, Firefox is free, and it has many benefits including security enhancements, and compatibility with the free Adblock Plus add-on, which will block annoying adverts as you browse the web. Anyway, here's how Firefox can be set to control your cookies...
Firstly, select Options from the main Firefox menu, and you'll see the dialogue box shown below...
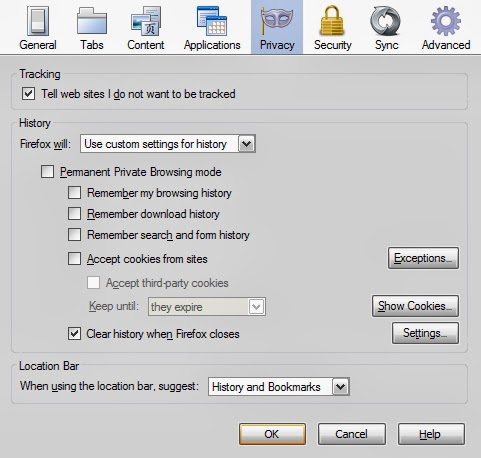
Select the Privacy tab along the top of the box, then tick/untick the boxes as I've done in the illustration above, making sure your dialogue box looks exactly the same as mine. Once you've done that, all cookies will be automatically blocked, and your browser will clear all browsing data each time you shut it down.
Next click on the Exceptions button. This will bring up a new dialogue, like the one below, but initially empty...

You now need to type in the domains (websites) you're going to allow to place and read cookies on your computer. You don't need the 'http://' bit - just the main domain name, such as 'www.google.co.uk', as I've typed in to my dialogue box above. Once you've typed in your domain name, you have two options. You can either click Allow, or Allow for Session. The domain name then drops down into the list box signalling that you're accepting cookies from that site. Clicking Allow will mean that cookies placed on your computer by your selected site will stay there until they expire. Clicking Allow for Session will mean that cookies for your selected site will be deleted when you close the browser. However, the browser will still accept new cookies from that site when you re-open it.
You can see in my example that I've set some sites to Allow, and others to Allow for Session. Ideally, I only want to allow for session, because that minimises the possibility of the individual sites monitoring my actions. However, some sites will not remember my password if I don't let them place a permanent cookie on my system. Those are the sites I've set to Allow. In all cases, I tried the Allow for Session option initially. If I then had to retype a password each time I wanted to use the site, I changed Allow for Session to Allow. To make things easier (but less private), you could simply set all your chosen sites to Allow.
And that's it. When you visit new sites during Google searches etc, you're secure in the knowledge that they're not putting cookies on your system, or (more importantly) reading cookies. And most importantly of all, you'll no longer have a band of ad barons marching around the web in your footsteps.
UPDATE: I've now added an article about the increasingly prevalent LSO cookies. These are nowhere near as widely used as the standard cookies discussed in this article, but when they are used, they evade conventional detection processes and they would not be deleted or blocked by any of the practices explained in this article. If you want to know how to control LSO cookies, please see LSO 'Super Cookies' - The Invisible Spy.

